

ETHICAL HACKING
Jul 10, 2014
9.95k likes | 23.18k Views
ETHICAL HACKING. PRESENTED By :. Sarjerao M engane. CONTENT. INTRODUCTION. METHODOLOGY. REPORTING. HISTORY. CONCLUSION . TYPES OF HACKERS. ETHICAL HACKING. ADVANTAGES AND DISADVANTAGES. HACKING . CONCLUSION. ETHICAL HACKING COMMANDMENTS. REFERENCE.
Share Presentation
- ethical haching org
- skilled hacker
- ethical hacking
- www wikipedia seminartopics
- united states air force

Presentation Transcript
PRESENTED By : SarjeraoMengane
CONTENT • INTRODUCTION • METHODOLOGY • REPORTING • HISTORY • CONCLUSION • TYPES OF HACKERS • ETHICAL HACKING • ADVANTAGES AND • DISADVANTAGES • HACKING • CONCLUSION • ETHICAL HACKING • COMMANDMENTS • REFERENCE
INTRODUCTION • Ethical hacking also known as penetration testing • or White-hat hacking, involves the same tools, • tricks and techniques that hackers use, but with • one major difference that ethical hacking is legal. • Ethical hacking can also ensure that vendors • claims about the security of their products • legitimate.
SECURITY • Security is the condition of being protect against • danger or loss. In the general sense, security is a • concept similar to safety. • Information security means protecting information • and information systems from unauthorized access, • use, disclosure, disruption, modification or destruc- • tion. Need for security There may be several forms of damages which are obviously interrelated which are produced by the intruders.
HISTORY HIGHLIGHTS • In one early ethical hack, the United States Air Force • conducted a “security evaluation” of the Multiuse • operating systems for “potential use as a two-level • (secret/top secret) systems.” • Most notable of these was the work by Farmer and • Venom, which was originally posted to Usenet in • December of 1993.
HACKING • Eric Raymond, compiler of “The New Hacker’s Dictionary”, • defines a hacker as a clever programmer. • A “Good hack” is a clever solution to a programming • problem and “hacking” is the act of doing it.
TYPE OF HACKERS • Black-Hat Hackers- • -----Ethical Hacker • White-Hat Hackers • -----Cracker • Grey-Hat Hackers • ----- Skilled Hacker
ETHICAL HACKING • A methodology adopted by ethical hackers to discover • the vulnerabilities existing in information systems • operating environments. • With the growth of the internet, computer security has • become a Major concern for businesses and govern- • ments. • Evaluate the intruder threat to their interests would be • to have independent computer security professionals • attempt to break into their computer systems.
Required Skills of an Ethical Hacker : • Microsoft : • Linux : • Firewalls : • Routers : • Network Protocols : • Project Management :
Reconnaissance: This literal meaning of the Word reconnaissance means a preliminary survey to gain the information . This is also known as foot-printing. As given in the analogy, this is the stage in which the hacker collects information about the company which the personal is going to hack. This is one of the pre-attacking phases. • Scanning: The hacker tries to make a blue print of the target network. The blue print includes the IP addresses of the target network which are live, the services which are running on those systems and so on Modern port scanning uses TCP protocol to do scanning and they could even detect the operating systems running on the particular hosts.
Password Cracking: There are many methods for cracking the password and then get in to the system. The simplest method is to guess the password. But this is a tedious work. But in order to make this work easier there are many automated tools for password guessing like legion. • Privilege escalation Privilege escalation is the process of raising the privileges once the hacker gets in to the system The privilege escalation process usually uses the vulnerabilities present in the host operating system or the software. There are many tools like hk.exe, metasploit etc. One such community of hackers is the metasploit
Ethical hacking tools: Ethical hackers utilize and have developed variety of tools intrude into different kinds of systems and to evaluate the security levels. The nature of these tools differs widely.
Certifications 1)CISE(Cetified into security expert) 2) AFCEH(AnkitFadia Certified Ethical Hacker)
Advantagesanddisadvantages: Ethical hacking nowadays is a backbone of network security .Each day its relevance is increasing ,the major pros & cons of ethical hacking • Advantages • “To catch a thief you have to think like a thief” • Help in closing the open holes in the network • Provides security to banking and financial • establishments • Prevents website defacements • An evolving technique
Future enhancements: • As it an evolving branch the scope of enhancement in technology is immense. No ethical hacker can ensure the system security by using the same technique repeatedly. He would He would have to improve , develop and explore new avenues repeatedly. • More enhanced software’s should be used for optimum protection . Tools used , need to be updated regularly and more efficient ones need to be developed
Conclusion • One of the main aim of the seminar is to make others understand that there are so many tools through which a hacker can get into a system. Its various perspectives. • Student • A student should understand that no software is made with zero Vulnerability. So while they are studying they should study the various possibilities and should study how to prevent that because they are the professionals of tomorrow
REFERENCE • www.scribd.com • www.wikipedia/seminartopics/ethical haching.org • www. Seminarsonly/ethical hacking.com
THANKYOU…!!!
- More by User

ETHICAL HACKING...
ETHICAL HACKING. INDEX. Ethical Hacking Terminology. What is Ethical hacking? Who are Ethical hacker? How many types of hackers? White Hats (Ethical hackers) Black Hats (Malicious hackers) Gray Hats (Good or bad hackers) How to Be Ethical ? The Phases of Ethical Hacking . Reconnaissance
1.36k views • 18 slides

Ethical Hacking
Wilfridus Bambang ( [email protected]). Ethical Hacking. Overview. Old School Hackers: History of Hacking Ec -Council: Certified Ethical Hacker Learning Competencies Hacking Tools Hacker Challenge Websites Additional Web Sites. Old School Hackers: History of Hacking .
1.24k views • 65 slides

Ethical Hacking: Hacking GMail
Ethical Hacking: Hacking GMail. What do Hackers Do?. Get into computer systems without valid accounts and passwords Take over Web servers Collect passwords from Internet traffic Take over computers with remote access trojans And much, much more. Ethical Hackers.
537 views • 10 slides

Ethical Hacking. License to hack. OVERVIEW. Ethical Hacking ? Why do ethical hackers hack? Ethical Hacking - Process Reporting Keeping It Legal . What is Ethical Hacking ?. It is legal Permission is obtained from the target Identify vulnerabilities visible from Internet
1.95k views • 12 slides

ETHICAL Hacking
ETHICAL Hacking. Eyüp ÇELİK BİLGİ TEKNOLOJİLERİ GÜVENLİK UZMANI. Hacking Evresi. Hacking Evresi. Password Cracking. Active Online Attack. Dictionary Attack. Brute-Force Attack. Keylogger. Donanimsal Keyloggerlar. YAZILIMSAL KEYLOGGERLAR. TROJANLAR. PaSSIVE ONLINE ATTACK. SNIFFING.
820 views • 26 slides

Ethical Hacking. Keith Brooks CIO and Director of Services Vanessa Brooks, Inc. Twitter/Skype: lotusevangelist [email protected]. Adapted from Zephyr Gauray’s slides found here: http://www.slideworld.com/slideshow.aspx/Ethical-Hacking-ppt-2766165
1.79k views • 34 slides

Ethical Hacking. CISS 301 Orientation Summer 2012. Instructor: Buddy Spisak. Office Hours: Monday’s 6:30 -7:40 p.m. in BS-143 (Jun. 11 to Jul. 30, 2012) I am also available through email or you can chat with me using Microsoft’s Windows Messenger (when I am available).
628 views • 29 slides

Ethical Hacking. CISS 301 Orientation Summer 2013. Instructor: Buddy Spisak. Office Hours: Monday 7:30 -8:30 p.m. in BS-143 (Jun. 10 to Jul. 29, 2013) I am also available through email, or you can chat with me using Microsoft ’ s Windows Messenger (when I am available).
534 views • 29 slides

Computer Science Innovations, LLC. Ethical Hacking. Overview. Define Security Discretionary Access Control Trusted Computer System Evaluation Criteria (TCSEC) - Orange Book 1984 by MITRE Corporation Basis for all we do in Security Define Security, how me measure it. Long-term goal.
1.74k views • 133 slides

Ethical Hacking. Pratheeba Murugesan. HACKER. AENDA. What is Ethical Hacking? Who are ethical hackers? Every Website-A Target Get out of jail free card Kinds of Testing Final Report. Ethical Hacking.
715 views • 10 slides
An ethical hacker is a computer and networking expert who systematically attempts to penetrate a computer system or network on behalf of its owners for the purpose of finding security vulnerabilities that a malicious hacker could potentially exploit.
265 views • 8 slides

Ethical Hacking Training- Chandigarh School of Ethical Hacking
http://www.ethicalhackingchandigarh.com/ethical-hacking-courses-in-chandigarh-mohali/ Chandigarh School of Ethical Hacking is 6 Weeks, 6 Months Ethical Hacking, Certified Ethical Hacking, Cyber Security Training provider in Chandigarh
177 views • 1 slides

Be the best ethical Hacker of today's World.Get your self admitted with the best ethical hacking in Delhi that will provide you 100% placement assistance and a popular certificate
336 views • 6 slides
Ethical Hacking Course | Hacking Course
Triad square infosec pvt ltd is one of the india best training IT institute .we have list of software programing training, information security training and consulting and these programs helps the individual their skills & knowledge for better prospects.
117 views • 2 slides

Ethical Hacking: Overview
Ethical Hacking: Overview. Presented By Team Neptune { Eric, Amy, Aung, Sophia, Venus Mae}. Ethical Hacking Principles Managing Incidents Exploring Security Policies Creating Security Policies SANS Web Application Security Policy. Topic Overview. Ethical Hacking Principles.
801 views • 48 slides

Ethical Hacking. AGENDA. What is Ethical Hacking? Who are ethical hackers? Every Website-A Target Get out of jail free card Kinds of Testing Final Report. Ethical Hacking. Independent computer security Professionals breaking into the computer systems.
419 views • 9 slides

277 views • 10 slides

ETHICAL HACKING. Presentation By: FATHIMA SHIMNA S3 ECE ROLL NO: 31. What is Hacking?. Hacking refers to an array of activities which are done to intrude some one else’s personal information space so as to use it for malicious, unwanted purposes.
773 views • 19 slides
Today's security is that the main downside and every one the work is finished over the net mistreatment knowledge. whereas the information is out there, there square measure many varieties of users who act with knowledge and a few of them for his or her would like it all for his or her gaining data. There square measure numerous techniques used for cover of information however the hacker or cracker is a lot of intelligent to hack the security, there square measure 2 classes of hackers theyre completely different from one another on the idea of their arrange. The one who has smart plans square measure referred to as moral hackers as a result of the ethics to use their talent and techniques of hacking to supply security to the organization. this idea describes concerning the hacking, styles of hackers, rules of moral hacking and also the blessings of the moral hacking. Mukesh. M | Dr. S. Vengateshkumar "Ethical Hacking" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-3 | Issue-6 , October 2019, URL: https://www.ijtsrd.com/papers/ijtsrd29351.pdf Paper URL: https://www.ijtsrd.com/engineering/computer-engineering/29351/ethical-hacking/mukesh-m
541 views • 3 slides
JavaScript seems to be disabled in your browser. For the best experience on our site, be sure to turn on Javascript in your browser.
Newly Launched - AI Presentation Maker

AI PPT Maker
Powerpoint Templates
PPT Bundles
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
Top 10 Ethical Hacking It Powerpoint Presentation Slides PowerPoint Presentation Templates in 2024
Ethical hacking is an essential aspect of cybersecurity, aimed at identifying vulnerabilities and strengthening the security posture of organizations. Utilizing PowerPoint presentation slides specifically designed for ethical hacking allows professionals to effectively communicate complex concepts and methodologies to diverse audiences, from technical teams to management. These PPTs can cover various topics, including penetration testing, network security, risk assessment, and compliance with industry standards.The use cases for ethical hacking PowerPoint presentations are vast. For instance, security professionals can employ these slides to conduct training sessions, ensuring that employees understand the importance of cybersecurity and the role of ethical hacking in safeguarding sensitive information. Additionally, organizations can use these presentations during security audits or assessments to showcase their commitment to proactive security measures. By illustrating real-world scenarios and case studies, ethical hacking PPTs help demystify the hacking process, making it more accessible to non-technical stakeholders. Furthermore, these presentations can serve as valuable tools for securing buy-in from upper management for cybersecurity initiatives, demonstrating the potential risks of neglecting ethical hacking practices. Overall, customizable PowerPoint slides enhance the effectiveness of communication in the realm of ethical hacking, fostering a culture of security awareness and proactive defense strategies.

Ethical hacking it powerpoint presentation slides
Deliver an informational PPT on various topics by using this Ethical Hacking IT Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with eighty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
This PowerPoint presentation gives a brief idea about the ethical hacking training provider company, problems that ethical hackers can solve, and reasons to choose ethical hacking as a profession. Here is an efficiently designed Ethical Hacking IT template. We have covered skills required to become an ethical hacker, including roles, responsibilities, description, and an overview of hacking and ethical hacking by including the need, purpose, types, and legality of ethical hacking. Moreover, in this Ethical Hacking and Network Security slides, we have included fundamental concepts of ethical hacking, benefits, limitation of ethical hacking, different types of ethical hackers, and critical vulnerabilities found by them. In addition, this Ethical Hacking PPT contains other ethical hacking techniques, various phases of ethical hacking such as surveillance, scanning, gaining access, maintaining access, clearing tracks, and best ethical hacking tools and software. Furthermore, this Ethical Hacking and Network Security template compares white and black hat hackers and ethical hacking and penetration testing. Lastly, this deck comprises a timeline, a roadmap, and a dashboard for ethical hacking. Download our 100 percent editable and customizable Hacking it ppt now.
- Problems Ethical Hackers Can Solve
- What Is Hacking
- What Is Ethical Hacking
- Types Of Ethical Hacking
- Is Ethical Hacking Legal
Related Products
Icons slide for ethical hacking it ppt powerpoint presentation file graphics pictures
Presenting our well crafted Icons Slide For Ethical Hacking It Ppt Powerpoint Presentation File Graphics Pictures set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
Our Icons Slide For Ethical Hacking It Ppt Powerpoint Presentation File Graphics Pictures are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
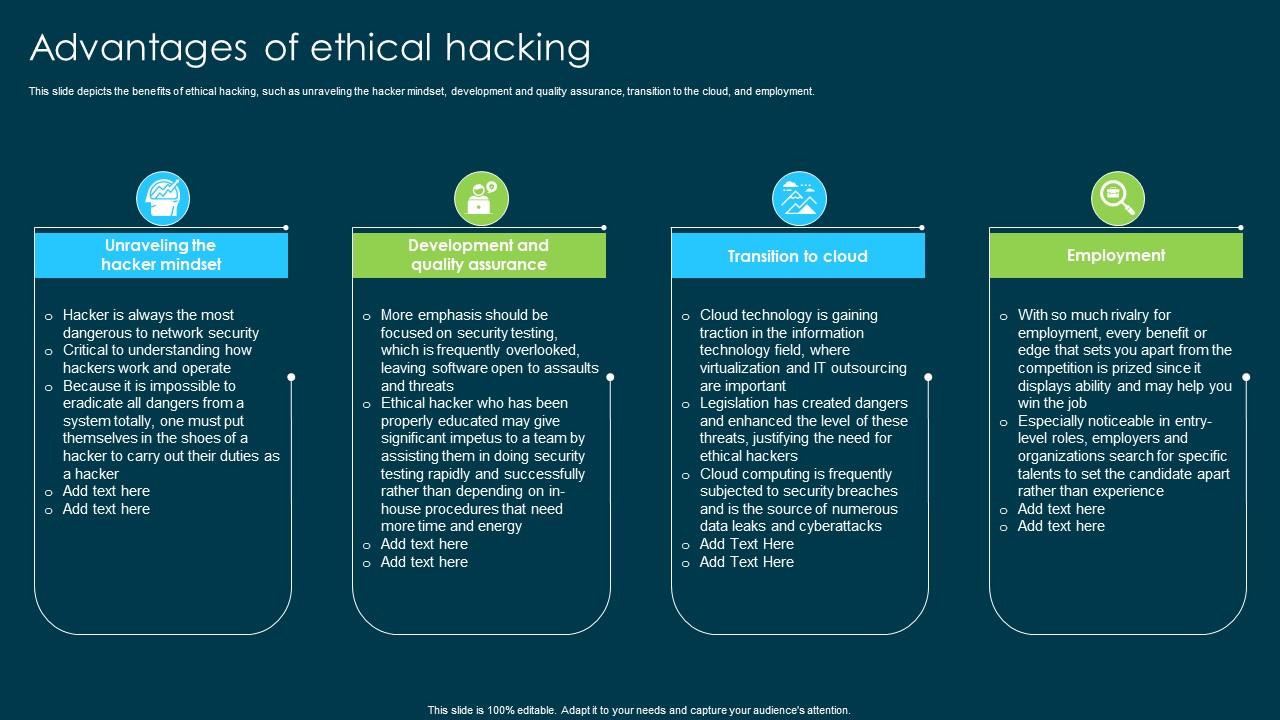
Ethical Hacking And Network Security Advantages Of Ethical Hacking
This slide depicts the benefits of ethical hacking, such as unraveling the hacker mindset, development and quality assurance, transition to the cloud, and employment. Introducing Ethical Hacking And Network Security Advantages Of Ethical Hacking to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Unraveling The Hacker Mindset, Development And Quality Assurance, Transition To Cloud, Employment, using this template. Grab it now to reap its full benefits.
This slide depicts the benefits of ethical hacking, such as unraveling the hacker mindset, development and quality assurance, transition to the cloud, and employment.
- Unraveling The Hacker Mindset
- Development And Quality Assurance
- Transition To Cloud

Ethical Hacking And Network Security Importance Of Ethical Hacking
This slide shows the importance of ethical hacking and how ethical hackers can help observe the organizational systems from the hackers viewpoint. Introducing Ethical Hacking And Network Security Importance Of Ethical Hacking to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Government Organizations, Sensitive And Essential Data Daily, Terrorist Organizations, Hacking Teams, using this template. Grab it now to reap its full benefits.
This slide shows the importance of ethical hacking and how ethical hackers can help observe the organizational systems from the hackers viewpoint.
- Government Organizations
- Sensitive And Essential Data Daily
- Terrorist Organizations
- Hacking Teams

Ethical Hacking And Network Security What Is Ethical Hacking
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. Introducing Ethical Hacking And Network Security What Is Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Professionals, Security Flaws, Ethical Hacking, Computer System, Application, using this template. Grab it now to reap its full benefits.
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.
- Security Professionals
- Security Flaws
- Ethical Hacking
- Computer System
- application

Ethical Hacking And Network Security Ethical Hacking Phase 1 Reconnaissance
This slide illustrates the reconnaissance phase of ethical hacking and how attackers use the foot printing technique to collect user information before the attack. Introducing Ethical Hacking And Network Security Ethical Hacking Phase 1 Reconnaissance to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Target To Gain Information, Hackers Can Exploit Social Media, Public Websites, Public Resources, using this template. Grab it now to reap its full benefits.
This slide illustrates the reconnaissance phase of ethical hacking and how attackers use the foot printing technique to collect user information before the attack.
- Target To Gain Information
- Hackers Can Exploit Social Media
- Public Websites
- Public Resources
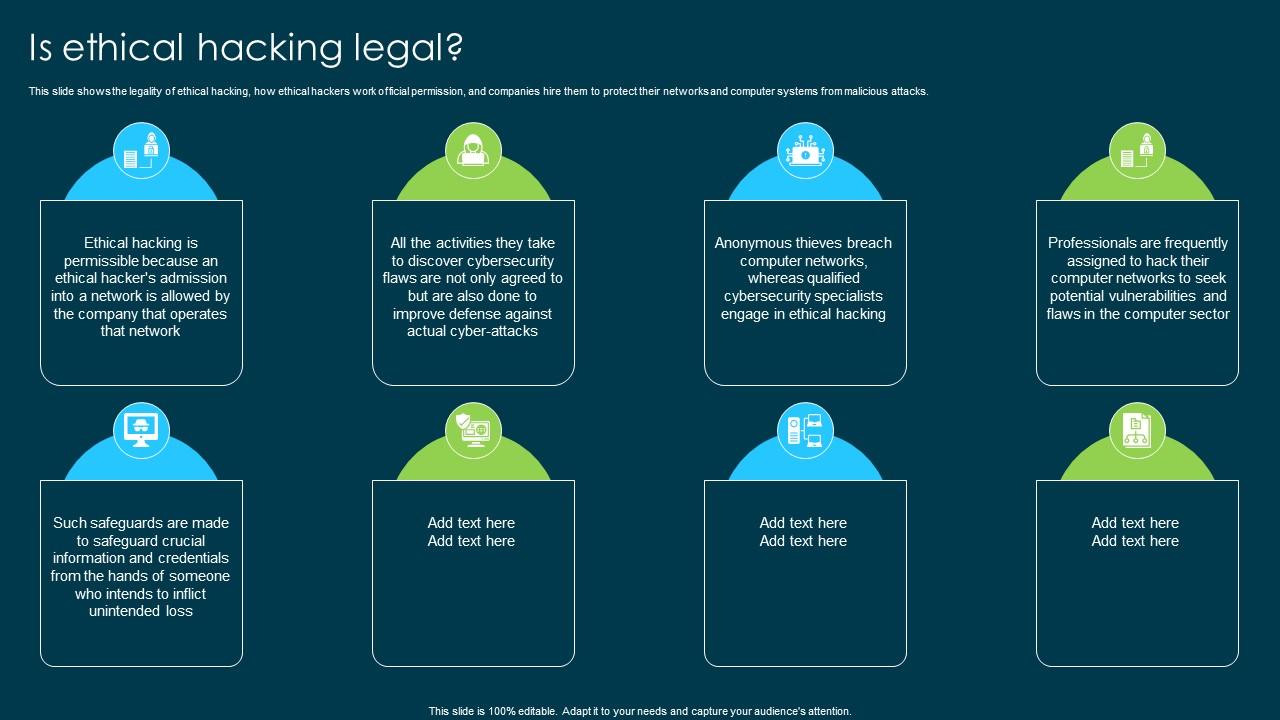
Ethical Hacking And Network Security Is Ethical Hacking Legal
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Is Ethical Hacking Legal. This template helps you present information on eight stages. You can also present information on Ethical Hacking, Computer Networks, Seek Potential Vulnerabilities, Inflict Unintended Loss using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.
- Computer Networks
- Seek Potential Vulnerabilities
- Inflict Unintended Loss

Ethical hacker and why we need ethical hacker hacking it
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. Deliver an outstanding presentation on the topic using this Ethical Hacker And Why We Need Ethical Hacker Hacking It. Dispense information and present a thorough explanation of Applications, Evaluate, Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance.
- applications

Ethical Hacking And Network Security Growth Of Ethical Hacking Profession
This slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Growth Of Ethical Hacking Profession. Dispense information and present a thorough explanation of Growth Of Ethical Hacking Profession, Computer Forensics Engineer, Ethical Hacker, Network Security Engineer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
This slide represents the growth of the ethical hacking profession, including annual salary, hiring companies, and designation such as information security officer, computer forensics engineer, ethical hacker, and network security engineer.
- Growth Of Ethical Hacking Profession
- Computer Forensics Engineer
- Ethical Hacker
- Network Security Engineer

Ethical Hacking And Network Security Roadmap For Ethical Hacking Program
This slide describes the roadmap for ethical hacking, including the phases of the ethical hacking training program to become a certified ethical hacking master. Introducing Ethical Hacking And Network Security Roadmap For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap For Ethical Hacking, Ethical Hacking Training Program, Ethical Hacking Master, using this template. Grab it now to reap its full benefits.
This slide describes the roadmap for ethical hacking, including the phases of the ethical hacking training program to become a certified ethical hacking master.
- Roadmap For Ethical Hacking
- Ethical Hacking Training Program
- Ethical Hacking Master


Ethical Hacking Seminar PPT with pdf report
Ethical Hacking Seminar and PPT with pdf report : Ethical hacking is also known as penetration testing or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference that Ethical hacking is legal.
Also See: Android PPT
Ethical Hacking is used in closing the open holes in the system network. It also provides security to banking and financial establishments and prevents website defacements. But there are some disadvantages of ethical hacking such as:
- All depends upon the trustworthiness of the ethical hacker
- Hiring professionals is expensive.
- Types of Hackers
- Black Hat Hacker
- White Hat Hacker
- Grey Hat Hacker
- Hacking Process
- Foot Printing
- Gaining Access
- Maintaining Access
Also See: Digital Signature PPT
- Required Skills of an Ethical Hacker
- Microsoft: skills in operation, configuration and management.
- Linux: knowledge of Linux/Unix; security setting, configuration, and services.
- Firewalls: configurations, and operation of intrusion detection systems.
- Routers: knowledge of routers, routing protocols, and access control lists
- Network Protocols: TCP/IP; how they function and can be manipulated.
Content of the Seminar and pdf report for Ethical Hacking
- Introduction
- Ethical Hacking
- Why do We need Ethical Hacking
- What do hackers do after Hacking?
- Disadvantages
- Future Enhancements
Also See: Digital Watermarking PPT
Here we are giving you Ethical Hacking Seminar and PPT with PDF report. All you need to do is just click on the download link and get it.
Ethical Hacking PPT and Seminar Free Download
Ethical Hacking pdf Report Free Download
It was all about Ethical Hacking Seminar and PPT with pdf report. If you liked it then please share it or if you want to ask anything then please hit the comment button.

Related Posts
50 research paper topics for mca students, 500+ bca project topics: projects ideas for bca students, mobile ppt presentation free download: definition and uses, web development ppt: definition, classification and tools, cloud storage seminar ppt and pdf report, semantic web seminar ppt and pdf report for free download, 5 comments already.
please upload report on penetration testing.
thanks for your recent uploads. please i will need ppt and pdf on thin client computing.
please also upload on Ransomware
How can we hack I’d??? Will u guide me???
this is illegal…grow up
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .

- About Amigo
- News Corner
- Our Ecosystem
- Become Partner
- Data Security Products
- File Security
- Email Security
- Siccura Guards
- Organization Security Testing
- Web app Penetration testing
- Mobile App Penetration Testing
- Network Penetration Testing
- Source Code Review
- Certification Course
- Certification in Ethical Hacking
- Certification in Network Security
- Certification in Digital Forensic
- Cyber Workshop
- Cyber Awarnress Program
- Cyber School Program
- Cyber Hygine Training
- Corporate Cyber Training
- Employer Security Training
- Employer Security Program
- Management Security Program
- Under Graduation Programs
- BSc Cyber Security & Cyber Forensics
- BCA in Cyber Security
- B.tech in Cyber Security
- B.tech in AI
- Post Graduation Programs
- MSc Cyber Security & Cyber Forensics
- MCA in Cyber Security
- PG Diploma in Cyber Security & Digital Forensics
- BSc MSc Cyber Security & Cyber Forensics
- M.tech in Cyber Security
- PG Diploma in Digital Marketing
- Case Studies
- Cyber Warrior
- Hall of Fame
- HK9 Community
- Under Attack
- Pre- Assesment
- Events Webniar

- Digital Forensic
- Ethical Hacking in Practice: Real-World Case Studies
Venkatalakshmi Madapati
Ethical hacking in practice Ethical hacking in practice involves the systematic process of identifying and exploiting vulnerabilities in computer systems, networks, or applications with the permission of the system owner or administrator. The primary goal is to assess the security posture of the target system and recommend measures to mitigate potential risks. Authorization and Consent Ethical hackers, also known as penetration testers or white-hat hackers, must obtain explicit authorization from the organization or individual responsible for the target system before conducting any security assessments. This authorization ensures that the hacking activities are conducted within legal and ethical boundaries. Methodologies Ethical hacking follows established methodologies to systematically evaluate the security of a target system. Common methodologies include reconnaissance, scanning, enumeration, exploitation, and post-exploitation. These steps involve gathering information about the target, identifying potential entry points, exploiting vulnerabilities, and maintaining access to assess the impact. Tools and Techniques Ethical hackers leverage a variety of tools and techniques to perform their assessments. These may include network scanners, vulnerability scanners, password cracking utilities, packet sniffers, and exploit frameworks. Additionally, they may employ social engineering tactics to manipulate users into divulging sensitive information or compromising security controls. Reconnaissance The first phase of ethical hacking involves gathering information about the target system, including its architecture, network topology, software versions, and potential entry points. This information is collected through passive reconnaissance techniques, such as public information gathering and network scanning. Vulnerability Assessment Ethical hackers use automated scanning tools and manual techniques to identify vulnerabilities in the target system. This includes software vulnerabilities, misconfiguration, weak passwords, and insecure network protocols. Vulnerability assessment helps prioritize security risks and potential attack vectors. Exploitation Once vulnerabilities are identified, ethical hackers attempt to exploit them to gain unauthorized access to the target system. This may involve using exploit code, social engineering tactics, or other techniques to bypass security controls and escalate privileges. The goal is to demonstrate the impact of the vulnerabilities and simulate real-world attack scenarios. Post-Exploitation After gaining access to the target system, ethical hackers conduct further analysis to determine the extent of the compromise and identify sensitive data or critical assets that may be at risk. This phase involves maintaining access, gathering additional information, and documenting the steps taken during the assessment. Reporting Ethical hackers document their findings and recommendations in a detailed report, which is provided to the organization or individual who authorized the assessment. This report typically includes an executive summary, technical details of vulnerabilities, risk assessment, and prioritized recommendations for remediation. The goal is to assist the organization in improving its security posture and mitigating potential risks effectively. Continuous Improvement Ethical hacking is an ongoing process that demands continuous learning and adaptation to keep pace with evolving threats and technologies. Ethical hackers stay informed about the latest security trends, tools, and techniques through training, certifications, and participation in the cybersecurity community. By continuously refining their skills, ethical hackers can effectively identify and address emerging vulnerabilities, contributing to the overall resilience of cybersecurity defenses. Real-World Case Studies we will analyze some notable ethical hacking case studies of this practice and how it has to securing our digital world. Case Study 1: The Target Breach In 2013, the retail giant Target fell victim to a massive data breach that the personal and financial of millions of . The breach was traced back to a malware that infiltrated the point-of-sale system.Ethical hackers were called in to investigate the incident and identify the security vulnerabilities that led to the breach.The analysis revealed that the gained initial access through a attack on one of the third-party vendors. Once inside the network, they exploited weak security controls and lack of to move laterally and access the payment system. This case study highlights the of security testing and continual to prevent such breaches. Case study 2: Stuxnet And Industrial Control S Stuxnet is arguably one of the most examples of cyber-attacks. in 2010, this sophisticated worm targeted industrial control systems (ICS)with a primary focus on Iran’s nuclear program. Ethical hackers played a crucial role in analyzing Stuxnet to its and mitigate its effects.The analysis of Stuxnet revealed that it unknown in Windows systems and Siemens control systems. It multiple , including exploits, rootkit installation, and worm-like , to target and manipulate specific logic (PLCs)The case study emphasizes the of robust security measures for critical and the need for continuous monitoring and response. Case Study 3: The Ashley Hack In 2015, the infamous Ashley Madison website, which facilitated affairs, a data breach. The breach exposed , including names, email addresses, and details, of millions of users. Ethical hackers were engaged to investigate the incident and assess the security practices of the website.The analysis several flaws, including weak password hashing , access controls, and poor data . , the lack of a robust incident plan and user data stored further the impact of the breach. This case study serves as a that even websites dealing with impact breach and information must prioritize security to protect user privacy. Conclusion Ethical hacking is a crucial practice for assessing and strengthening cybersecurity defenses in today’s digital world. Through explicit authorization, systematic methodologies, and the use of various tools and techniques, ethical hackers identify vulnerabilities and recommend measures to mitigate risks. Real-world case studies, such as the Target breach, Stuxnet attack, and Ashley Madison hack, highlight the importance of proactive security testing, continuous improvement, and robust incident response measures. These case studies underscore the ongoing need for organizations to prioritize security to safeguard against potential breaches and protect sensitive data. By learning from past incidents and embracing a culture of security, businesses can better defend against evolving cyber threats and enhance their overall resilience in the face of adversity.
Previous Post
Ethical Hacking Ethics
Ceh certification: what employers look for and how to stand out, post a comment cancel reply.
Your email address will not be published.
Leave a Reply
Email address
Website Url
Save my name, and email in this browser for the next time I comment.

Related Posts

IDS/IPS: Boosting Forensics for Proactive Threat Defense
Intrusion Detection Systems (IDS)An Intrusion Detection System (IDS) is a security tool designed to monitor…

Remote Work Revolution: Companies Embrace Digital Collaboration Tools for Seamless Operations
Remote Work Revolution: Companies Embrace Digital Collaboration Tools for Seamless Operations The remote work revolution…

Blockchain Innovation Sparks Surge in Decentralized Finance Projects
What is a Blockchain ? Blockchain is a decentralized digital ledger technology that enables the…

Securing the Connected World: Navigating IoT Security Challenges
Securing the Connected World: Navigating IoT Security Challenges Securing the connected world in the era…
Newsletter Sign Up!
For information Consult with our expert members

Our Company
- Our Echo System
Cyber Education
- Employee Security Program
- BSc Cyber Security & Cyber Forensics
- PG Diploma in Cyber Security & Digital Forensics
- BSc MSc Cyber Security & Cyber Forensics
- Terms of use
- Privacy and Cookies Policy
Your message (optional)

Denounce with righteous indignation and dislike men who are beguiled and demoralized by the charms pleasure moment so blinded desire that they cannot foresee the pain and trouble.
Latest Projects


Ethical Hacking Case Study: Times When Hackers Avoided Setbacks
Home Blog Security Ethical Hacking Case Study: Times When Hackers Avoided Setbacks
Over the years, there has been a huge rise in cybercrime attacks due to the general public's lack of knowledge about hacking and internet-related crimes. Unfortunately, this goes for both common people as well as big companies. People generally think that having an antivirus that offers cyber security is enough for them to stay safe on the internet. The same goes for big corporations that do not use high-quality protection for their data. This is where ethical hackers come into play with some really impressive ethical hacking cases where they saved the day.
Ethical Hacking - An Overview
Bypassing or breaking through the security mechanisms of a system to search for vulnerabilities, data breaches, and other possible threats is an example of ethical hacking. It has to be done ethically to comply with the laws and regulations relevant to the area or the company. Because an individual must go through several procedures to get into a system and record it, this form of infiltration is referred to as "penetration testing" in the industry jargon. This is because an individual must record the system after entering it.
You must be wondering what ethical hackers are? They are people who possess the same knowledge as hackers but use this knowledge to boost internet protection protocols and software. You, too, can learn how to be an ethical hacker using a CEH certification training course. They are the ones who protect us from actual hackers. There are multiple categories of ethical hackers, such as:
- Black hat hackers: They use their knowledge for malicious intent, blackmail, etc.
- White hat hackers: They possess the same knowledge as the black hat hackers but use their knowledge to help companies increase their defenses against the black hat hackers.
How Do White Hat Hackers Work?
With the growing rise in hackers on the internet, companies have begun using ethical hackers to scope out the flaws and vulnerabilities in their software and protection programs. But, how do these ethical hacking cases work? These people use the same techniques as Black hat hackers to penetrate a company's defenses. By doing so, they can understand the safety flaws. This gives them the inside edge to patch the flaws to ensure that hackers cannot get through the protection.
There have been multiple instances where ethical hackers have been able to spot cracks in a company's security and save them from having huge security leaks due to hackers, which would result in huge losses. The following ethical hacking case study is six instances where ethical hackers were able to save a company from dealing with data leaks and suffering huge financial losses.
Case Studies of Ethical Hacking
1. a crack in wordpress leaked user information.
Back in 2019, a new plugin was released for WordPress called Social Network Tabs. As you know, most people use WordPress to make their websites. This plugin got very popular, but none knew about the vulnerability. It basically helped users share their website content on social media.
Baptiste Robert was a French security researcher who was known online by his user handle, Elliot Alderson. He was the one who found the crack in the plugin, which was given the ID CVE-2018-20555 by MITRE. You can find this case and similar ones in a case study on ethical hacking PDF online.
You must be wondering what exactly did this flaw in the plugin do? The flaw in the plugin compromised the user's Twitter account. Since the plugin is connected to the user's social media account, the vulnerability leaked the user's social media details. Robert was the first to spot this leak and was fast to notify Twitter about it, which helped secure the user's accounts that got affected by it.
2. Oracle's vulnerability in their WebLogic servers
In 2019, Oracle released a security update without any prior notice. This took fans by surprise until they learned why this happened. The security patch was a very critical update that fixed a code vulnerability in the WebLogic Server.
The flaw was brought to light by a security firm known as KnownSec404. The vulnerability was labeled as CVE-2019-2729 which received a level of 9.8/10, which is pretty high. The vulnerability left it open to be attacked by hackers targeting two applications that the server left open to the internet.
3. Visa card vulnerability that allowed for a bypass in payment limits
This was one of the most famous ethical hacking cases brought to light on the internet. It took place on July 29th, 2019. Two security researchers from a company called Positive Technologies spotted a security weakness in Visa contactless cards that allowed hackers to bypass the payment limits. This flaw in their security would cost the company a huge loss. This one case boosted the interest in ethical hacking. As a result, multiple students began taking cyber security course certificates online to learn more.
Tim Yunusov, the Head of Banking security, and Leigh-Anne Galloway, the Cyber Security Resilience Lead, were the ones who discovered this. This was made public after five major UK banks were targeted. The contactless verification had a limit of £30 on Visa cards, but due to this weakness, hackers could bypass this limit.
4. Vulnerabilities allow for ransomware in Canon DSLR
In 2019, the DefCon27 was held, which was attended by Eyal Itkin. He was a vulnerability researcher at Check Point Software Technologies. He revealed that the Canon EOS 80D DSLR had a vulnerability that the PTP, which was the Picture Transfer Protocol, had an issue whereby ransomware could be transferred into the DSLR using the WiFi connection.
He went on to highlight that there were six vulnerabilities in the PTP that made it an easy target for hackers. They could easily get into the DSLR using this crack in the firmware. The objective of the hackers was simple. Infiltrate the DSLR and infect it with ransomware that would render the pictures useless to the user. The user would have to pay a ransom to get the pictures back to the hacker.
The team working with Eyal informed Canon about the security breach vulnerability. A few months later, Canon released a notice saying that the vulnerability was never exploited by hackers, which means that it was never discovered. However, they also announced that users should take safety precautions to keep themselves safe.
5. Zoom on the Mac could be hacked and expose the camera
On July 9th, 2019, Jonathan Leitschuh exposed a very critical vulnerability in Appel's Macs. This flaw in the security framework allowed hackers to take control of the user's front camera. As a result, many websites could force a user into a Zoom call without their knowledge or permission. This was something that invaded privacy, and millions of people who would conduct meetings or even use Zoom, in general, were at risk. This is an important ethical hacking case as it was broken on social media to make people aware. The very same day, Apple sent out a fix that was a simple patch that users could download and install to fix the issue. Zoom, too, didn't waste any time by issuing a quick-fix patch to stop the issue.
6. A backdoor could allow hackers to execute root commands on servers
DefCon27 was where many ethical hacking cases came to light. Another one was the case of Özkan Mustafa Akkuş, who was a Turkish security researcher. They exposed a vulnerability in Webmin, a web-based system configuration in Unix-like systems.
The vulnerability was labeled CVE-2019-15107; it was a backdoor entry that allowed hackers to execute commands with root privileges. This left users exposed to hackers that could take control of their systems or hold it for ransom.
This is an important ethical hacking case study as Jamie Cameron, who is the author of Webmin, claimed that the backdoor was set by an employee. This was something that wasn't known to the company. They announced a new patch update to the new software version, which would be released to all the users.
A very important case study to know about that was featured in the case study of ethical hacking PDF was that of Zomato in India.
7. What happened to Zomato?
In 2017 a hacker broke into the security of Zomato, one of the biggest online restaurant guides and food ordering apps. The hacker was after five things.
- Names
- Emails
- Numeric user IDs
- User names
- Passwords
The amount of data lost was in the millions as 17 million users were targets. The hacker was able to put up this information on the darknet for anyone to buy before starting talks with the company. This was one of the most shocking ethical hacking cases in India. This also led people to question the cyber security of the country.
Once this case was exposed to the public, Zomato issued a few blogs where they spoke about the real person behind this breach. It was said that the work was done by an ethical hacker who wanted to bring the issue of national cyber security to light. It worked as the whole country began talking about cyber security.
8. The bug bounty program
This was a reward program started to get talented individuals to use their hacking skills to expose the weaknesses in the company's security programs. Today, multiple companies use this program to find the issues in their security. Companies like Google, Microsoft, and Facebook have invested millions in this program to find the flaws in their system and make them stronger against cyber-attacks.
The individual can get cash awards or even recognize if they can point out and fix the issue. This has brought to light multiple numbers of issues as well as many talented, ethical hacker cases that we have ever seen.
Many people are now interested in taking up ethical hacking as their career. You can get the KnowledgeHut’s CEH certification training to learn more about ethical hacking.
In conclusion, ethical hackers are essential to the cyber security field. They are the ones who can figure out the flaws in any system and the ones who can also provide quick fixes. They are important to know how to keep your data safe in these troubled times. If you wish to know more about ethical hacking, you can get the case study on ethical hacking PDF, which you can find online. These case studies are important as they highlight the weakness in online security firmware. These need to be fixed as they could mean a potential data leak which could result in a huge financial and reputation loss for the companies that suffer it. Employing White Hat hackers is one way of fighting against it.
Frequently Asked Questions (FAQs)
An example of ethical hacking done by White Hat hackers is simulating an attack on a system to see if there are any flaws in the system. They can also use the information found online about the company to find a way to infiltrate the company's security.
The role of an ethical hacker is simple. They possess the same knowledge as Black Hat hackers. But, the only difference is that they use their knowledge to spot the flaws in security systems so that they can fix them. They just want to make the security impenetrable to any attacks.
The five steps are:
- Reconnaissance: This step is about understanding the network and security features.
- Scanning: This is where they scan for the flaws in the system to see if there could be any entry.
- Gain Access: This is where they gain access to the system by any means necessary.
- Maintain Access: This is where they keep their presence inside the security software or firmware without alarming anyone or losing access to the system.
- Cover Tracks: This is where they cover up any tracks they left while getting inside or leaving the system.

Vitesh Sharma
Vitesh Sharma, a distinguished Cyber Security expert with a wealth of experience exceeding 6 years in the Telecom & Networking Industry. Armed with a CCIE and CISA certification, Vitesh possesses expertise in MPLS, Wi-Fi Planning & Designing, High Availability, QoS, IPv6, and IP KPIs. With a robust background in evaluating and optimizing MPLS security for telecom giants, Vitesh has been instrumental in driving large service provider engagements, emphasizing planning, designing, assessment, and optimization. His experience spans prestigious organizations like Barclays, Protiviti, EY, PwC India, Tata Consultancy Services, and more. With a unique blend of technical prowess and management acumen, Vitesh remains at the forefront of ensuring secure and efficient networking solutions, solidifying his position as a notable figure in the cybersecurity landscape.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
This repository contains resources for the Ethical Hacking course offered by Internshala. The course is designed to provide learners with an in-depth understanding of ethical hacking techniques, tools, and methodologies, as well as the legal and ethical aspects of hacking.
Hritik-Shirsath/Ethical-Hacking-Course-Internshala-PPT
Folders and files, repository files navigation, ethical hacking course internshala ppt, course overview.
- Course Name: Ethical Hacking
- Course Provider: Internshala
- Course Duration: 8 weeks
- Course Level: Beginner to Intermediate
- Course Language: English
Course Curriculum
The course covers a wide range of topics related to ethical hacking, including but not limited to:
- Introduction to Ethical Hacking
- Footprinting and Reconnaissance
- Scanning Networks
- Enumeration
- System Hacking
- Malware Threats
- Social Engineering
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
- Web Application Penetration Testing
- Wireless Network Hacking
- Cryptography
- Cloud Computing and IoT Security
- Mobile Hacking
- Incident Handling and Response
- Ethics and Legal Aspects of Hacking
The resources in this repository are intended for educational purposes only, as part of the Ethical Hacking course offered by Internshala. Learners are expected to follow ethical and legal guidelines when using the techniques, tools, and methodologies learned in the course. The repository is regularly updated with new resources, and learners are encouraged to check for updates periodically.
The course and the resources in this repository are not intended to promote or support any illegal activities, including unauthorized access to computer systems, networks, or data. The learners are responsible for using the knowledge gained from the course in an ethical and legal manner, and the course provider and repository maintainers are not liable for any misuse of the resources or techniques learned in the course.
Contributing
Contributions to this repository are welcome in the form of bug reports, feature requests, or additional resources that can enhance the learning experience of the course. Please submit a pull request or create an issue if you would like to contribute.

IMAGES
VIDEO
COMMENTS
INTRODUCTION • Ethical hacking also known as penetration testing • or White-hat hacking, involves the same tools, • tricks and techniques that hackers use, but with • one major difference that ethical hacking is legal. • Ethical hacking can also ensure that vendors • claims about the security of their products • legitimate.
By illustrating real-world scenarios and case studies, ethical hacking PPTs help demystify the hacking process, making it more accessible to non-technical stakeholders. ... this Ethical Hacking PPT contains other ethical hacking techniques, various phases of ethical hacking such as surveillance, scanning, gaining access, maintaining access ...
Download ppt "Some "Ethical Hacking" Case Studies" Similar presentations . Chapter 1: Fundamentals of Security JV Note: Images may not be relevant to information on slide. 1 Defining System Security Policies. 2 Module - Defining System Security Policies ♦ Overview An important aspect of Network management is to protect your.
Also See: Digital Watermarking PPT. Here we are giving you Ethical Hacking Seminar and PPT with PDF report. All you need to do is just click on the download link and get it. Ethical Hacking PPT and Seminar Free Download. Ethical Hacking pdf Report Free Download. It was all about Ethical Hacking Seminar and PPT with pdf report.
Ethical hacking in practice Ethical hacking in practice involves the systematic process of identifying and exploiting vulnerabilities in computer systems, networks, or applications with the permission of the system owner or administrator. The primary goal is to assess the security posture of the target system and recommend measures to mitigate potential risks. Authorization and Consent
The following ethical hacking case study is six instances where ethical hackers were able to save a company from dealing with data leaks and suffering huge financial losses. Case Studies of Ethical Hacking 1. A crack in WordPress leaked user information. Back in 2019, a new plugin was released for WordPress called Social Network Tabs.
This repository contains resources for the Ethical Hacking course offered by Internshala. The course is designed to provide learners with an in-depth understanding of ethical hacking techniques, tools, and methodologies, as well as the legal and ethical aspects of hacking.
Ethical hacking also known as penetration testing or white-hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference that Ethical hacking is legal. Ethical hacking is performed with the target's permission. The intent of ethical hacking is to discover vulnerabilities from a
Ethical Hacking Definition of a ethical hacker, "A person who hacks into a computer network in order to test or evaluate its security, rather than with malicious or criminal intent." Also known as White Hat Hackers Companies will hire talented ethical hackers to find any vulnerabilities or flaws in their code. Certified Ethical Hacker